POP and IMAP
在 Red Hat 中,網路郵件存取通訊協定 (Internet Messages Access Protocol, IMAP) 和郵局通訊協定 (Post Office Protocol, POP) 是使用 dovecot 套件,它是 System V 管理服務,使用 /etc/init.d/ 中的腳本來啟動及關閉,支援 pop、pop3s、imap、imaps,它的加密是由 openssl 提供。
要啟動 dovecot,在套件安裝好之後就可以使用 System V 腳本來啟動:
# service dovecot start
正在啟動 Dovecot Imap: [確定]
檢查一下是否有啟動:
# netstat -tulpn | grep dovecot
tcp 0 0 :::993 :::* LISTEN 10655/dovecot (imaps)
tcp 0 0 :::995 :::* LISTEN 10655/dovecot (pop3s)
tcp 0 0 :::110 :::* LISTEN 10655/dovecot (pop)
tcp 0 0 :::143 :::* LISTEN 10655/dovecot (imap)
也可以用 telnet 到 110 埠檢查:
# telnet localhost 110
Trying 127.0.0.1…
Connected to localhost.localdomain (127.0.0.1).
Escape character is ‘^]’.
+OK Dovecot ready. (有反應了,表示已經啟動,可以用 QUIT 退出了,不想退出可以用 POP Protocol 來玩玩看)
USER kevin (輸入帳號,USER 也可以用小寫,用大寫只是讓本文好辨認)
+OK
PASS 12345 (輸入密碼)
+OK Logged in. (成功登入)
STAT (查詢一下)
+OK 2 1196 (有 2 封信,1196 Bytes)
LIST (列出信件)
+OK 2 messages: (2 封信,第 1 封有 597 Bytes,第 2 封有 599 Bytes)
1 597
2 599
.
RETR 1 (取得編號第 1 的信件)
+OK 597 octets (信件內容如下)
Return-Path: <root@localhost.localdomain>
Received: from localhost.localdomain (rhel5 [127.0.0.1])
by localhost.localdomain (8.13.8/8.13.8) with ESMTP id n3MFStIZ011095
for <kevin@localhost.localdomain>; Wed, 22 Apr 2009 23:28:55 +0800
Received: (from root@localhost)
by localhost.localdomain (8.13.8/8.13.8/Submit) id n3MFStYU011094
for kevin; Wed, 22 Apr 2009 23:28:55 +0800
Date: Wed, 22 Apr 2009 23:28:55 +0800
From: root <root@localhost.localdomain>
Message-Id: <200904221528.n3MFStYU011094@localhost.localdomain>
To: kevin@localhost.localdomain
Subject: test mail 01
test
.
DELE 1 (刪除編號 1 的信件)
+OK Marked to be deleted. (編號 1 的信件標記刪除)
RETR 2
+OK 599 octets
Return-Path: <root@localhost.localdomain>
Received: from localhost.localdomain (rhel5 [127.0.0.1])
by localhost.localdomain (8.13.8/8.13.8) with ESMTP id n3MFT4R5011113
for <kevin@localhost.localdomain>; Wed, 22 Apr 2009 23:29:04 +0800
Received: (from root@localhost)
by localhost.localdomain (8.13.8/8.13.8/Submit) id n3MFT4NG011112
for kevin; Wed, 22 Apr 2009 23:29:04 +0800
Date: Wed, 22 Apr 2009 23:29:04 +0800
From: root <root@localhost.localdomain>
Message-Id: <200904221529.n3MFT4NG011112@localhost.localdomain>
To: kevin@localhost.localdomain
Subject: test mail 02
test 2
.
DELE 2
+OK Marked to be deleted.
QUIT (離開)
+OK Logging out, messages deleted. (刪除標記刪除的信件)
Connection closed by foreign host. (結束連線)
==============================
SSL 加密
要啟用 SSL 加密認證,要先製作一個憑證並簽署:
# make -C /etc/pki/tls/certs dovecot.pem (或者至 /etc/pki/tls/certs 目錄中,直接 make dovecot.pem)
make: Entering directory `/etc/pki/tls/certs’
umask 77 ; \
PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
/usr/bin/openssl req -utf8 -newkey rsa:1024 -keyout $PEM1 -nodes -x509 -days 365 -out $PEM2 -set_serial 0 ; \
cat $PEM1 > dovecot.pem ; \
echo “” >> dovecot.pem ; \
cat $PEM2 >> dovecot.pem ; \
rm -f $PEM1 $PEM2
Generating a 1024 bit RSA private key
..++++++
..++++++
writing new private key to ‘/tmp/openssl.py2194’
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [GB]:TW (輸入認證資料)
State or Province Name (full name) [Berkshire]:Taiwan
Locality Name (eg, city) [Newbury]:Taipei
Organization Name (eg, company) [My Company Ltd]:ishm
Organizational Unit Name (eg, section) []:ishm
Common Name (eg, your name or your server’s hostname) []:ishm.idv.tw
Email Address []:admin@ishm.idv.tw
make: Leaving directory `/etc/pki/tls/certs’ (製作完成)
檢視一下 dovecot.pem 的內容:
# openssl x509 -noout -text -in dovecot.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=TW, ST=Taiwan, L=Taipei, O=ishm, OU=ishm, CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
Validity
Not Before: Apr 23 13:16:27 2009 GMT
Not After : Apr 23 13:16:27 2010 GMT
Subject: C=TW, ST=Taiwan, L=Taipei, O=ishm, OU=ishm, CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:c6:80:c8:7d:6d:d6:a1:dd:f9:a7:2e:9c:06:4c:
58:db:76:42:9f:d4:a3:be:a8:c1:19:6b:91:75:72:
2d:cf:76:48:77:e3:5b:fe:07:3f:f0:27:dc:8a:99:
4b:d0:ef:52:87:d7:1d:5f:20:80:ef:42:d5:dd:16:
32:12:88:c8:73:01:c6:b4:b4:a8:97:48:bc:e2:c0:
32:8c:74:17:3d:c0:19:3a:84:9c:0b:d7:d7:29:04:
36:7a:0d:02:e0:03:b3:ff:d8:d5:1d:20:d7:ac:84:
a1:cb:8b:c6:7e:32:75:b5:2d:8b:2b:25:f5:6f:94:
99:5d:84:84:e4:39:54:1d:dd
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
FB:04:D2:01:06:A0:BD:4C:A8:BB:6E:22:6B:82:AC:81:F7:6C:E8:19
X509v3 Authority Key Identifier:
keyid:FB:04:D2:01:06:A0:BD:4C:A8:BB:6E:22:6B:82:AC:81:F7:6C:E8:19
DirName:/C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
serial:00
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha1WithRSAEncryption
81:90:74:58:3e:e2:0a:d7:36:87:f0:84:da:82:4b:b0:ca:af:
e1:38:c4:09:03:c1:c8:ba:5c:c8:90:fb:07:60:9f:75:8b:17:
79:2b:1f:8c:cb:c6:5b:01:3b:37:66:cc:e4:0a:9f:de:aa:3e:
af:70:b7:d1:ce:a6:90:34:28:3d:55:ed:24:5f:27:d5:02:bb:
f3:78:d1:ae:b4:ed:f0:1e:53:47:2d:36:5c:dc:8c:8d:e2:2f:
f0:0b:d6:24:ce:45:fb:eb:42:a9:d3:2c:a2:27:3c:55:7a:58:
aa:05:f4:6f:30:2a:da:bc:b8:13:9f:33:13:b7:cd:19:8c:43:
fe:d7
接下來修改 /etc/dovecot.conf 中憑證的位置:
ssl_cert_file = /etc/pki/tls/certs/dovecot.pem
ssl_key_file = /etc/pki/tls/certs/dovecot.pem
重新啟動 dovecot:
# service dovecot restart
正在停止 Dovecot Imap: [確定]
正在啟動 Dovecot Imap: [確定]
用 openssl 來測試 POP3S 連線:
# openssl s_client -connect 192.168.0.2:995
CONNECTED(00000003) (以下是憑證檢驗區段)
depth=0 /C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
verify error:num=18:self signed certificate
verify return:1
depth=0 /C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
verify return:1
—
Certificate chain
0 s:/C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
i:/C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
—
Server certificate
—–BEGIN CERTIFICATE—–
MIIDaDCCAtGgAwIBAgIBADANBgkqhkiG9w0BAQUFADCBhTELMAkGA1UEBhMCVFcx
DzANBgNVBAgTBlRhaXdhbjEPMA0GA1UEBxMGVGFpcGVpMQ0wCwYDVQQKEwRpc2ht
MQ0wCwYDVQQLEwRpc2htMRQwEgYDVQQDEwtpc2htLmlkdi50dzEgMB4GCSqGSIb3
DQEJARYRYWRtaW5AaXNobS5pZHYudHcwHhcNMDkwNDIzMTMxNjI3WhcNMTAwNDIz
MTMxNjI3WjCBhTELMAkGA1UEBhMCVFcxDzANBgNVBAgTBlRhaXdhbjEPMA0GA1UE
BxMGVGFpcGVpMQ0wCwYDVQQKEwRpc2htMQ0wCwYDVQQLEwRpc2htMRQwEgYDVQQD
Ewtpc2htLmlkdi50dzEgMB4GCSqGSIb3DQEJARYRYWRtaW5AaXNobS5pZHYudHcw
gZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAMaAyH1t1qHd+acunAZMWNt2Qp/U
o76owRlrkXVyLc92SHfjW/4HP/An3IqZS9DvUofXHV8ggO9C1d0WMhKIyHMBxrS0
qJdIvOLAMox0Fz3AGTqEnAvX1ykENnoNAuADs//Y1R0g16yEocuLxn4ydbUtiysl
9W+UmV2EhOQ5VB3dAgMBAAGjgeUwgeIwHQYDVR0OBBYEFPsE0gEGoL1MqLtuImuC
rIH3bOgZMIGyBgNVHSMEgaowgaeAFPsE0gEGoL1MqLtuImuCrIH3bOgZoYGLpIGI
MIGFMQswCQYDVQQGEwJUVzEPMA0GA1UECBMGVGFpd2FuMQ8wDQYDVQQHEwZUYWlw
ZWkxDTALBgNVBAoTBGlzaG0xDTALBgNVBAsTBGlzaG0xFDASBgNVBAMTC2lzaG0u
aWR2LnR3MSAwHgYJKoZIhvcNAQkBFhFhZG1pbkBpc2htLmlkdi50d4IBADAMBgNV
HRMEBTADAQH/MA0GCSqGSIb3DQEBBQUAA4GBAIGQdFg+4grXNofwhNqCS7DKr+E4
xAkDwci6XMiQ+wdgn3WLF3krH4zLxlsBOzdmzOQKn96qPq9wt9HOppA0KD1V7SRf
J9UCu/N40a607fAeU0ctNlzcjI3iL/AL1iTORfvrQqnTLKInPFV6WKoF9G8wKtq8
uBOfMxO3zRmMQ/7X
—–END CERTIFICATE—–
subject=/C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
issuer=/C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
—
No client certificate CA names sent
—
SSL handshake has read 1440 bytes and written 340 bytes
—
New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHA
Server public key is 1024 bit
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1
Cipher : DHE-RSA-AES256-SHA
Session-ID: BC649AAFFFC9394522032599689C9B7DFE0E514C209A0621BAD8E9361034D48B
Session-ID-ctx:
Master-Key: 8A04EF246A08CF754C1E1277BEFA4F9D4CB5B418992CDD6FD841721FBBCDF382A76C20BD577285BB7C048A15D50B405E
Key-Arg : None
Krb5 Principal: None
Start Time: 1240493814
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
—
+OK Dovecot ready. (成功登入)
USER kevin
+OK
PASS 12345
+OK Logged in.
STAT
+OK 0 0 (沒有信件)
QUIT (退出)
DONE
用 openssl 來測試 IMAPs:
# openssl s_client -connect 192.168.0.2:993
CONNECTED(00000003)
depth=0 /C=TW/ST=Taiwan/L=Taipei/O=ishm/OU=ishm/CN=ishm.idv.tw/emailAddress=admin@ishm.idv.tw
verify error:num=18:self signed certificate
… 略 …
Master-Key: BA0A58602A0640843158F2054871984BA013B63CCC18C6C9FF22BDD55AD7833CA45C94C4913A6C37E955C5AA1CE0368D
Key-Arg : None
Krb5 Principal: None
Start Time: 1240497271
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
—
* OK Dovecot ready. (成功連線)
1 LOGIN kevin 12345 (數字1是序號,一定要有,用 kevin 密碼 12345 登入)
1 OK Logged in.
2 SELECT INBOX (選用收件匣)
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 2 EXISTS (有 2 封郵件)
* 2 RECENT (有 2 封新信)
* OK [UNSEEN 1] First unseen.
* OK [UIDVALIDITY 1240413822] UIDs valid
* OK [UIDNEXT 9] Predicted next UID
2 OK [READ-WRITE] Select completed.
3 FETCH 1 (FLAGS RFC822) (讀取第 1 封信)
* 1 FETCH (FLAGS (\Seen \Recent) RFC822 {608}
Return-Path: <root@localhost.localdomain>
Received: from localhost.localdomain (rhel5 [127.0.0.1])
by localhost.localdomain (8.13.8/8.13.8) with ESMTP id n3NEY0ua004915
for <kevin@localhost.localdomain>; Thu, 23 Apr 2009 22:34:00 +0800
Received: (from root@localhost)
by localhost.localdomain (8.13.8/8.13.8/Submit) id n3NEY0T6004914
for kevin; Thu, 23 Apr 2009 22:34:00 +0800
Date: Thu, 23 Apr 2009 22:34:00 +0800
From: root <root@localhost.localdomain>
Message-Id: <200904231434.n3NEY0T6004914@localhost.localdomain>
To: kevin@localhost.localdomain
Subject: NO1 TEST
1111111111111111111
)
3 OK Fetch completed.
4 FETCH 2 (FLAGS RFC822) (讀取第 2 封信)
* 2 FETCH (FLAGS (\Seen \Recent) RFC822 {624}
Return-Path: <root@localhost.localdomain>
… 略 …
To: kevin@localhost.localdomain
Subject: No2 Second TEST
2222222222222
2222222222222
)
4 OK Fetch completed.
5 STORE 1 +FLAGS \DELETED (將第 1 封信標記為刪除)
* 1 FETCH (FLAGS (\Deleted \Seen \Recent))
5 OK Store completed.
6 STORE 2 +FLAGS \DELETED (將第 2 封信標記為刪除)
* 2 FETCH (FLAGS (\Deleted \Seen \Recent))
6 OK Store completed.
7 EXPUNGE (執行標記動作..刪除)
* 2 EXPUNGE
* 1 EXPUNGE
* 0 RECENT
7 OK Expunge completed.
8 SELECT INBOX (檢查一下)
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 0 EXISTS (2 封信都刪除了)
* 0 RECENT
* OK [UIDVALIDITY 1240413822] UIDs valid
* OK [UIDNEXT 9] Predicted next UID
8 OK [READ-WRITE] Select completed.
9 LOGOUT (登出)
* BYE Logging out
9 OK Logout completed.
read:errno=0
==============================
mutt
除了用 telnet 和 openssl 來測試之外,在 Linux 文字模式中,也可用 mutt 指令來收取信件:
# mutt -f pop://USER@SERVER[:PORT]
# mutt -f pops://USER@SERVER[:PORT]
# mutt -f imap://USER@SERVER[:PORT]
# mutt -f imaps://USER@SERVER[:PORT]
例:
# mutt -f imaps://kevin@192.168.0.2
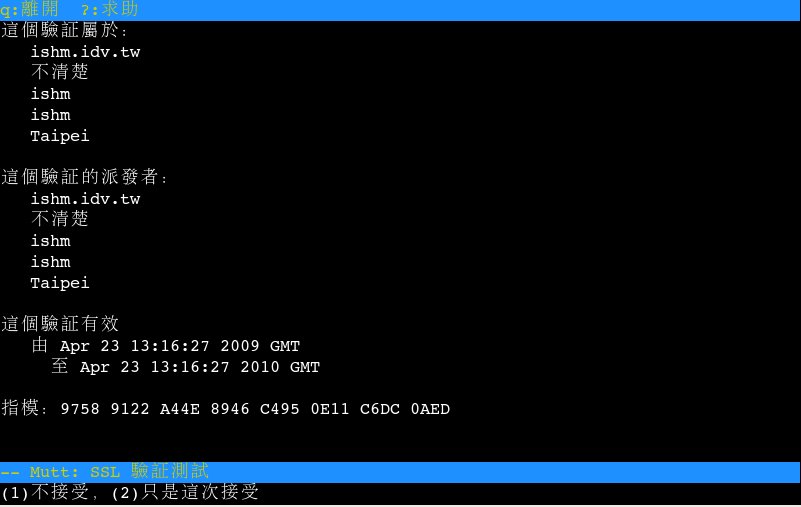
mutt 登入認證畫面
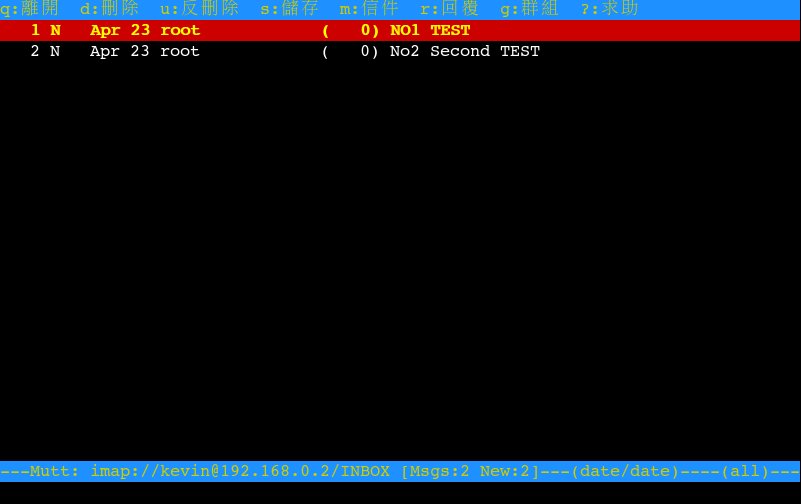
mutt 列表畫面
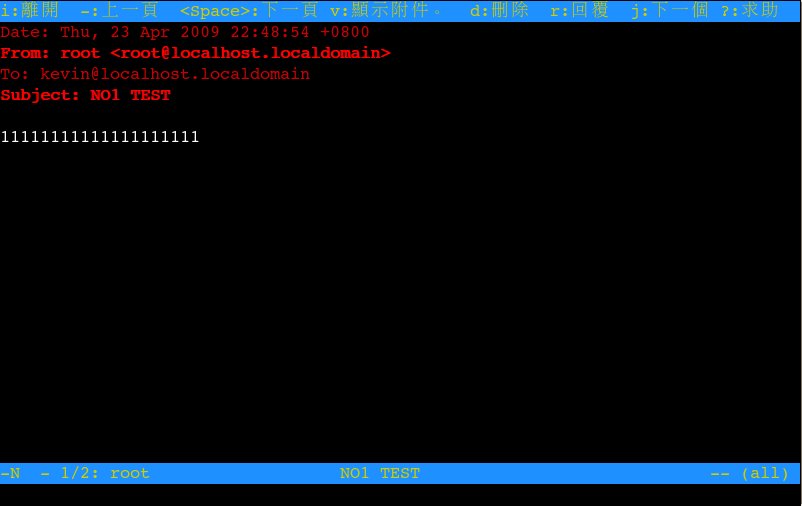
mutt 信件讀取畫面
